Since it's December and there's loads of Holiday CTF's and other fun things to do in spare time, I decided to hop into TryHackMe again to just practice some techniques in random rooms. Hadn't been on THM for a while but noticed that my 'Skills Matrix' on the site was glaringly deficient on Web Applications. A quick search for some free rooms turned up one called Corridor available here.
The room is an easy room but was certainly a quick/fun challenge. It also forced me to learn how to leverage ZAP's Fuzzing payload processor for a change. Normally I've not needed to do much else with ZAP's Fuzzing configurations beyond selecting a payload. So learning experience turned into blog post!
About the room: You have found yourself in a strange corridor. Can you find your way back to where you came?
In this challenge, you will explore potential IDOR vulnerabilities. Examine the URL endpoints you access as you navigate the website and note the hexadecimal values you find (they look an awful lot like a hash, don't they?). This could help you uncover website locations you were not expected to access.
Sounds like a good time so let's dive in!
Upon connecting to THM's VPN, the website for Corridor was accessible at htt[p]://10.10.103.96 and was quite literally a corridor of 'empty' rooms.
Clicking on any of the doors simply leads one to an empty room with no clear way on how to escape! Time to fire up ZAP to take a closer look at things (Yea yea, obviously ZAP is already opened in that screenshot!). With ZAP loaded up and FireFox proxying requests to ZAP, the site was spidered. This turned up some interesting requests for each of the 'doors'.
Interesting... Each request to the page corresponding to each door appears to be an MD5 hash! Let's see if they are crackable! Viewing the source of the mainpage, all the room links are visible and can be copied into another document and then John can be let loose on the hashes.
Well, John figured those out in a hurry... Looks like each MD5 hash simply corresponds to a number! That makes things easy. Since the name of the room is 'corrIDOR' and the description mentioned teaching about IDOR (Insecure Direct Objection Reference), there's probably a good chance there's some other hidden pages. There's a number of ways to check but let's leverage ZAP's fuzzing tool and practice using payload processors.
From one of the requests, right-click and mouse over 'Attack'. In the Attack sub-menu, click on 'Fuzz'.
From the Fuzzer window, the part of the request intended to be 'fuzzed' is the MD5 hash portion of the GET line. Highlight just the MD5 hash and then click on the 'Add...' button to add that location as a Fuzz location.
The next screen will prompt for a payload for this Fuzzer location. As determined earlier with John, the website appears to use MD5 hashes of the numbers 1 through 13 so let's try a range of numbers from 0 to 50 as our payload to see how the site responds. To do this, click the 'Add...' button in the Payloads window. In the new window that appears, click the drop down menu for 'Type' and select the type 'Numberszz'. Notice that the payload window will change and asks for some information about the numbers. Let's start from 0 and go to 50 incrementing by 1. Once done, click the 'Generate Preview' button and notice that the 'Payloads Preview' window should populate.
Assuming the payloads preview now shows the list of numbers, click the 'Add' button at the bottom of the window. Now it's time to tell ZAP to modify this list of numbers to reflect the MD5 hashes that the web application expects in the requests. ZAP calls this processing and can be done by highlighting the newly created payload and then clicking the 'Processors...' button from the payload window.In the 'Payload Processors' window that opens, click the 'Add...' button. Then under the 'Type:' drop-down, let's find the 'MD5 Hash' option and then click the 'Generate Preview' button to test the transformation. If all goes well the 'Processed Payloads' section should now show MD5 hashes of the corresponding number from the Payloads list!
If the MD5 hashes populated, then click the 'Add' button at the bottom. Then Click 'Ok' in the 'Payload Processors' window as this processor is now setup and ready to go. Finally, before closing the 'Payloads' window, confirm that ZAP is setup to apply everything that was just configured.
From the above screenshot, it looks like everything is ready to go. Let's Fuzz this website and hope to finding something useful to escape the Corridor! Click 'Ok' in the 'Payloads' window and then click 'Start Fuzzer' in the 'Fuzzer' window. Notice that the bottom section of the ZAP user interface will switch to the Fuzzer tab and show the requests being sent as well as the responses from the server. Since only 50 requests were being sent, this process won't take long.
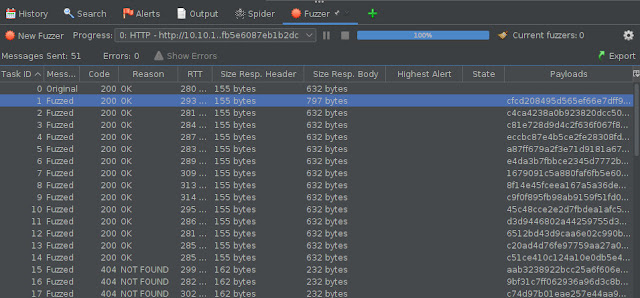
Notice in the Code/Reason sections that there is a number of 404 errors, meaning the webserver didn't have that page. Let's scroll back up to the top of the fuzzer history. Notice now that there's a bunch of 200 codes which often means the webserver found/returned something to the request! It was already noted that there were 13 doors but looking closer at the requests, 14 requests received 200 codes and one of those requests differs in size from the others; how interesting...
Let's see what that request looks like in the browser. Right click on the request and then select 'Copy URLs to Clipboard' to paste in the ZAP browser or click on 'Open URL in System Browser' to have ZAP open the link automatically in the system browser.Success! Zap helped to quickly try a bunch of possible pages even though the requests needed to be transformed before being sent. The payload could also be expanded to be an even large list of numbers or even words that are hashed in an attempt to "hide" pages from folks on the Internet.
Remember security through obscurity is typically frowned upon!